[#] Disclaimer
The content has been made available for informational and educational purposes only. All practices demos are performed on my own devices or networks, Infinity-Hacks are not responsible for any type of action. All videos and tutorials are for informational and educational purposes only. We believe that ethical hacking, information security, and cyber security should be familiar subjects to anyone using digital information and computers. We believe that it is impossible to defend yourself from hackers without knowing how hacking is done. All Videos are provided ( https://infinityhacks.net/ ). Is only for those who are interested to learn about ethical hacking, cyber security, penetration testing, and malware analysis. Hacking tutorials are against the misuse of information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used.
Product Terms and Conditions:
You agree not to reproduce, duplicate, copy, sell, resell, or exploit any portion of the course, use of the service, or access to the Service or any contact on the website through which the course is provided, without express written permission by us. The owner of the course deserves complete authority to block access to any customer of the course who violates the terms and conditions of the course. The product once purchased is not refundable after successful payment.
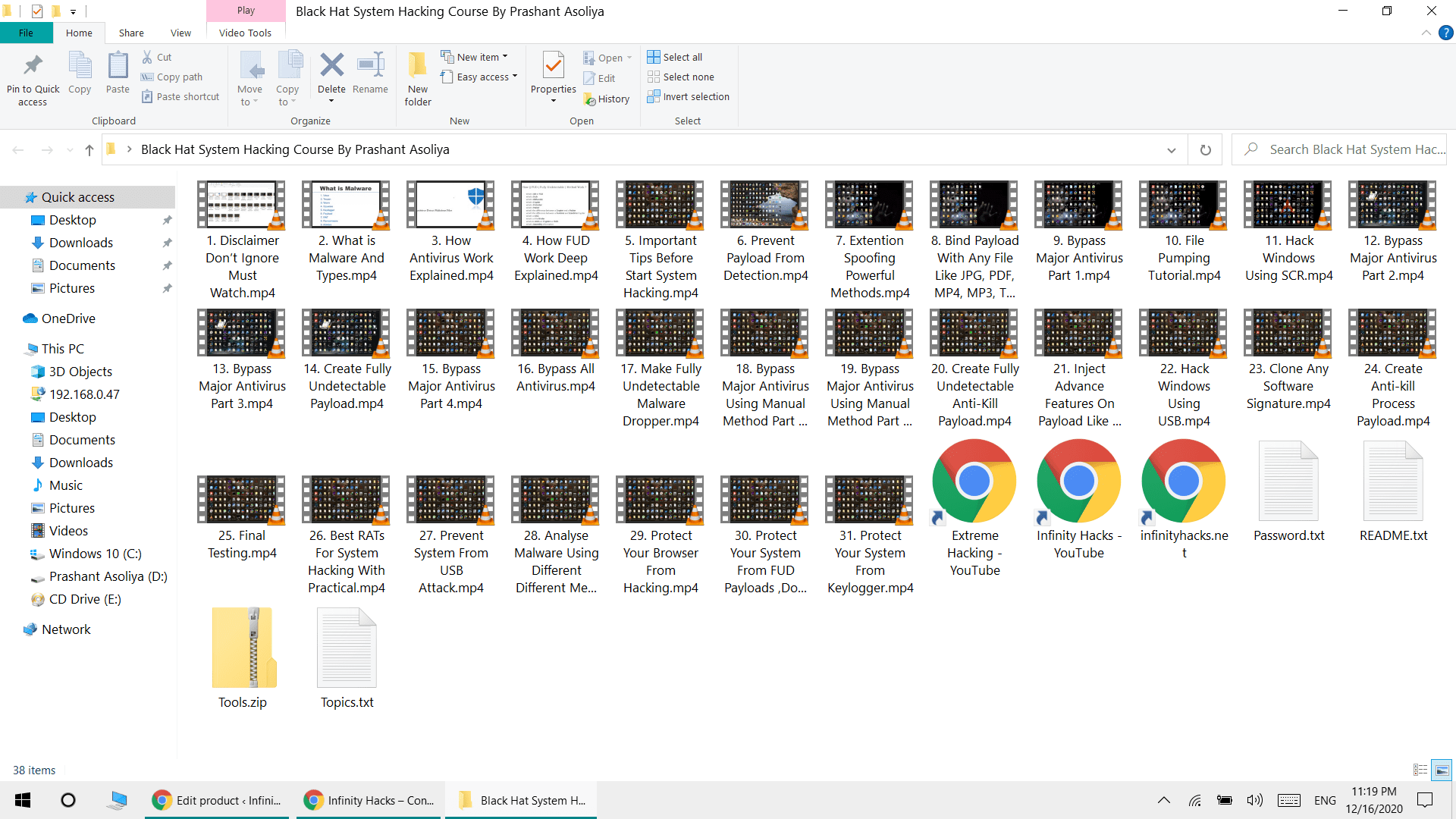
Topics
1. Disclaimer Don’t Ignore Must Watch
2. What is Malware And Types
3. How Antivirus Work Explained
4. How FUD Works Deep Explained
5. Important Tips Before Creating FUD Payloads
6. Prevent Payload From Detection
7. Extension Spoofing Powerful Methods
8. Bind Payload With Any File Like JPG, PDF, MP4, MP3, TXT, and many more
9. Bypass Major Antivirus Part 1
10. File Pumping Tutorial
11. Remotely Control Windows Using SCR
12. Bypass Major Antivirus Part 2
13. Bypass Major Antivirus Part 3
14. Create a Fully Undetectable Payload
15. Bypass Major Antivirus Part 4
16. Bypass All Antivirus
17. Make Fully Undetectable Malware Dropper
18. Bypass Major Antivirus Using Manual Method Part 5
20. Create a Fully Undetectable Anti-Kill Payload
21. Inject Advance Features On Payload Like Anti-kill Process, Persistent, And Many More
22. Remotely Control Windows Using USB
23. Clone Any Software Signature
24. Create an Anti-kill Critical Process Payload
25. Final Testing
26. Best RATs For System Hacking With Practical
27. Prevent System From USB Attack
28. Analyze Malware Using Different Types of Methods
29. Protect Your Browser From Hacking
30. Protect Your System From FUD Payloads, Doc Exploits, Hidden Processes, or Many More
31. Protect Your System From Keylogger
Minimum System Requirements
– Windows 8, 10, 11
– 4GB RAM
– 250GB HDD or SSD Space
– i3 4th Generation or Latest-Generation Processor




Abhay Singh –
Your explanation is on the next level i am very impressed by your course thanks for giving deep knowledge of hacking
Anil –
Powerful
Rahul Singh –
Best product for learn system hacking
TheMenaceee (verified owner) –
He is such a passionate teacher. he explains so well. This course will give you a full understanding of obfuscation and system hacking. You can easily bypass any anti-virus by taking his course. He has shown over 15 different ways thats the best part of this course. He has provided all the tools including rats. Nobody else will teach you in this manner. Look no further I highly recommend this course
Prashant Asoliya –
Thank you 😍
Supriya –
I have bypassed major antivirus using your methods😅 thank sir for this amazing course