[#] Disclaimer
The content has been made available for informational and educational purposes only. All practices demos are performed on my own devices or networks, Infinity-Hacks are not responsible for any type of action. All videos and tutorials are for informational and educational purposes only. We believe that ethical hacking, information security, and cyber security should be familiar subjects to anyone using digital information and computers. We believe that it is impossible to defend yourself from hackers without knowing how hacking is done. All Videos are provided ( https://infinityhacks.net/ ). Is only for those who are interested to learn about ethical hacking, cyber security, penetration testing, and malware analysis. Hacking tutorials are against the misuse of information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used.
Product Terms and Conditions:
You agree not to reproduce, duplicate, copy, sell, resell, or exploit any portion of the course, use of the service or access to the Service or any contact on the website through which the course is provided, without express written permission by us. The owner of the course deserves complete authority to block access to any customer of the course who violates the terms and conditions of the course. The product once purchased is not refundable after successful payment.
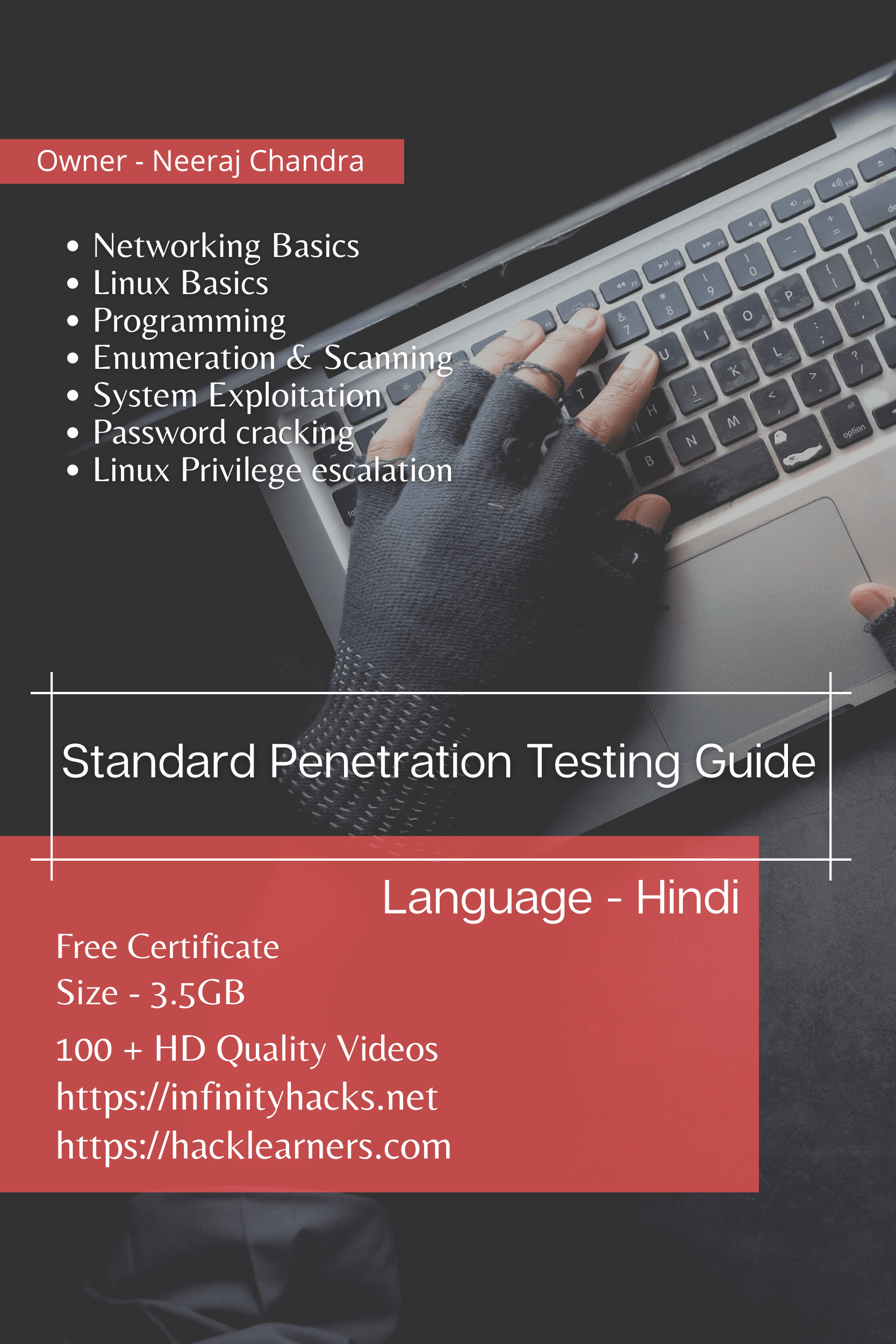
Description
This course is for those who want to learn ethical hacking and penetration testing at an affordable price.
What You’ll Learn
Networking Basics
Linux Basics
Programming
Enumeration & Scanning
System Exploitation
Password cracking
Linux Privilege escalation
and a lot more things you’ll learn from this course.
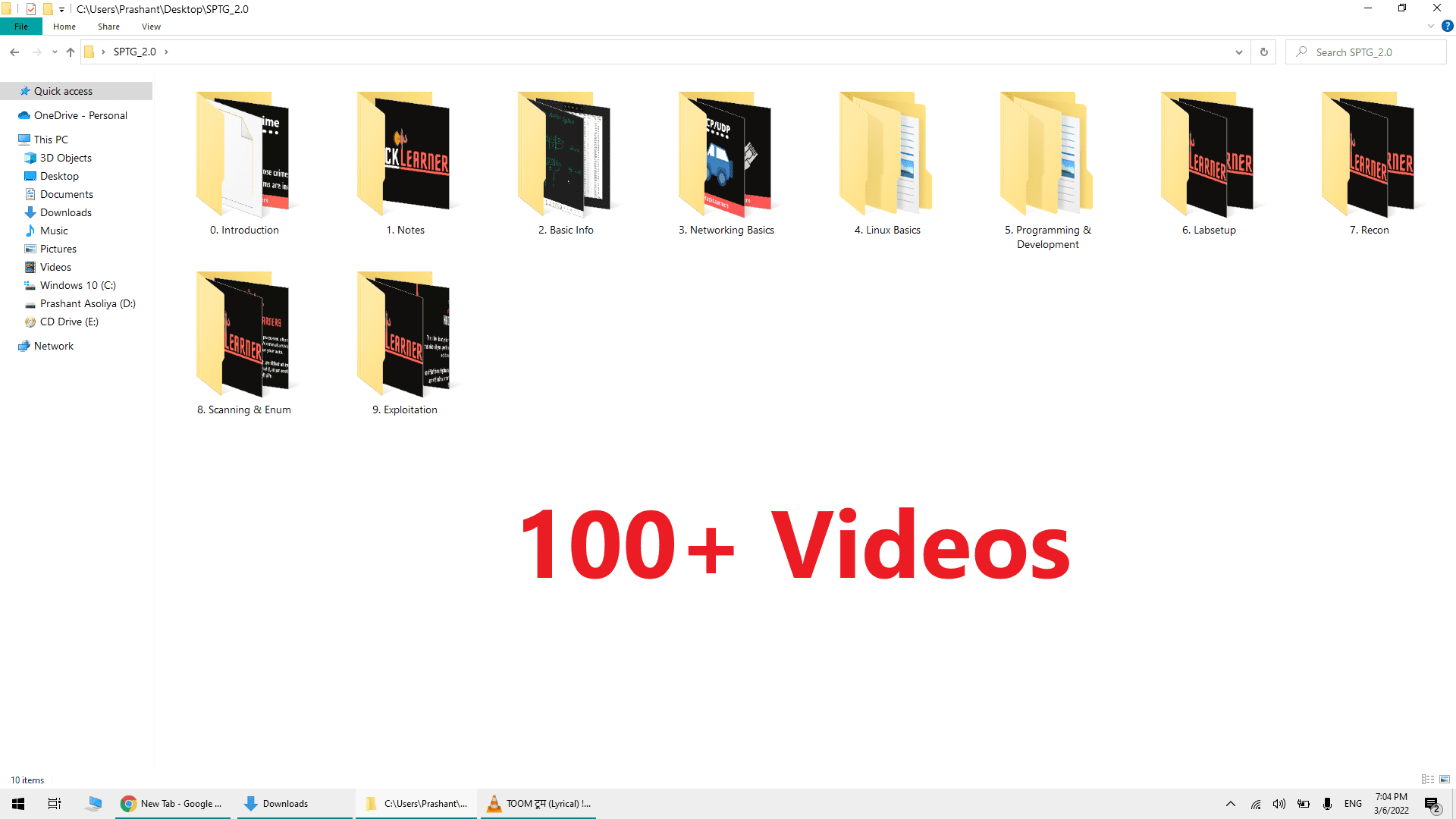
Topics
1. Indian Cyber Laws
2. How To Make Effective Notes
3. Markdown For Notes
4. Understanding Number System
5. Understanding Binary Conversion
6. Understanding Octal Conversion
7. Understanding Hexadecimal Conversion
8. Understanding Ascii System
9. Basic Of Networking
10. Networking Equipment & Key Terminologies
11. Open System Interconnection Model
12. TCP/IP Model
13. Information Protocol Address
14. Getting Familiar With Subnetting
15. Domain Name System
16. Transmission Control Protocol and User Datagram Protocol
17. Networking Ports
18. Virtual Private Network / Proxy / Socks
19. Getting Familiar With Linux
20. Understanding Shell
21. Basic Console Commands
22. User Identifier and Group Identifier
23. Linux Directory Structure
24. File Permission In Linux
25. Suid Bit in Linux
26. Sgid Bit in Linux
27. Sticky Bit
28. Linux Package Management
29. Secure Shell Connection
30. Pipe and Redirection
31. Linux Crontab
32. Searching Files Inside Linux
33. Hard Link and Soft Links
34. Hyper Text Markup Language
35. Creating Html Page
36. Heading and paragraph
37. Text Formatting
38. Link Management in Html
39. Playing with videos and images
40. Listing in Html
41. Creating Form with Html
42. Introduction To C Plus Plus
43. Setting Up Compiler and ide
44. Writing first cpp program
45. Understanding Variables and Data Types
46. Data Input and Output
47. Operators in cpp
48. If Else Conditions
49. Switch and Cases – Controlling statements
50. Storing Data in a row – Understanding Arrays
51. Repeating Tasks – Understanding Loops
52. Do While loop
53. For loop
54. Functions
55. Understanding Virtualization
56. Software Requirement For Lab setup
57. Setting Up Windows inside VM
58. Setting Up Kali Linux inside VM
59. Setting Vulnerable Lab
60. Creating Private Network
61. Adding New Vulnerable Machine
62. Phases of Hacking
63. Choosing Our Target
64. Recon With Windows
65. Getting Domain Info
66. Hunting For Subdomains
67. Understanding Google Hacking Technique
68. Looking back in web time
69. Hunting For Technologies
70. Discovering Hosts in a Network
71. Getting Familiar with NMAP-1
72. Advanced options in NMAP-2
73. Quick Port Scanner
74. FTP Login Check
75. Hunting For Hidden Directory
76. Scanning WordPress For loopholes
77. SMB share Enumeration Finding Intrusting Stuff
78. Hands on Metasploit
79. Gathering Information With Metasploit
80. Exploiting Target Weakness with Metasploit
81. Generating Payload and accessing Windows Machine With MSFvenom
82. Type Of Shells and it’s difference
83. Type of Malicious wares
84. Technique to Upgrade Shell
85. Moving Files between Target and Attacker
86. Finding Password Hashes – Linux
87. Finding Password Hashes – Windows
88. Creating SSH Tunnels
89. Escalating Privileges
90. Enumerating Target System
91. Escalating Privileges with scripts
92. Exploiting Target Kernel
93. Exploiting Vulnerable Paths
94. Cracking Passwords
95. Identifying Hash Type for Password Cracking
96. Cracking Hahes With John the Ripper
97. Cracking Password hash online
98. Searching Exploits
99. Exploiting Vulnerable Machine.
100. Exploiting Vulnerable machine-2.
Minimum System Requirements
- Windows 8, 10, 11
- 4GB of computer ram
- 250GB of HDD or SSD
- i3 4th gen or latest-gen
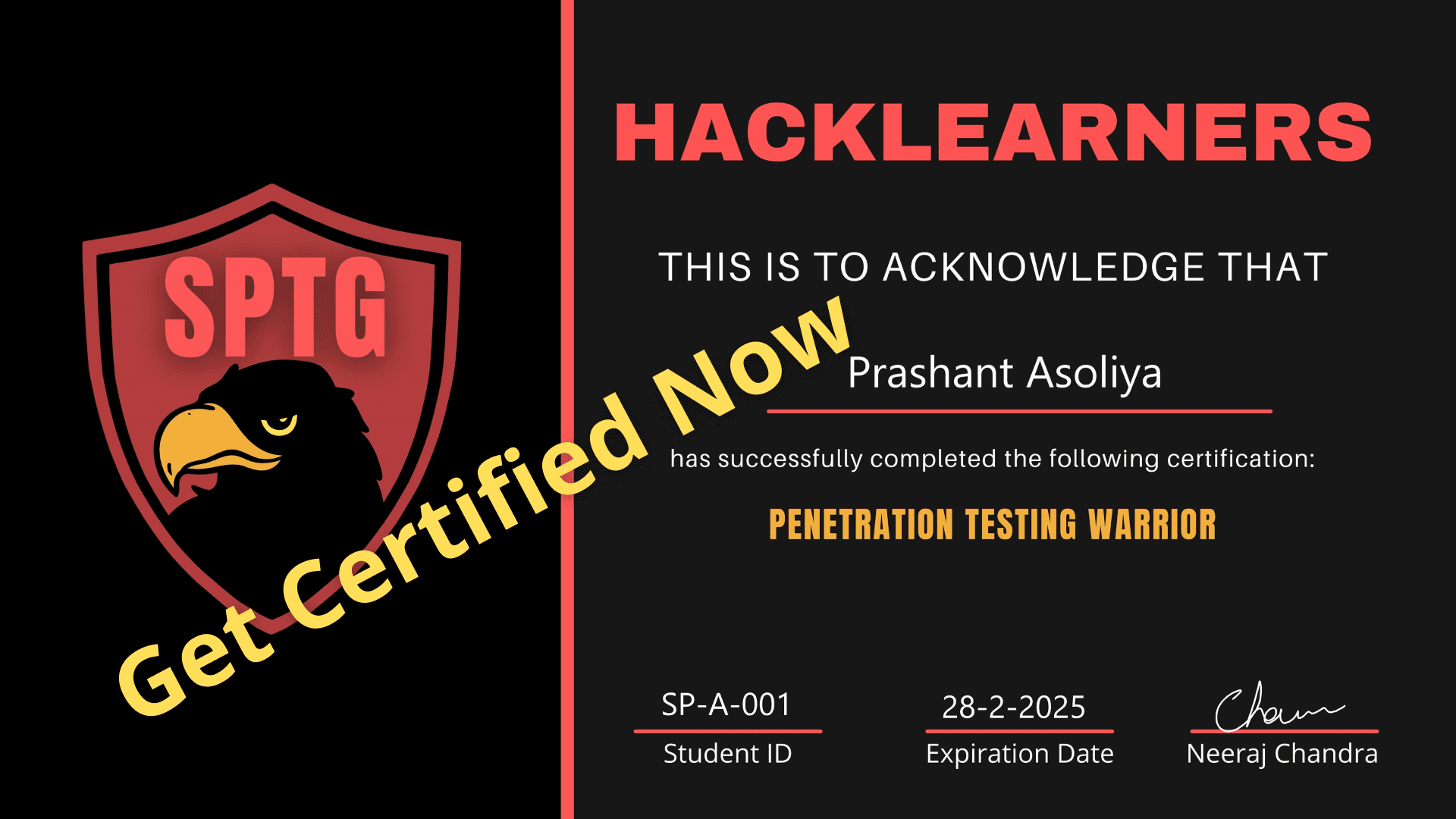
How do get the certificate?
To get the certification you have to give an exam once you pass that exam your certificate will be delivered to your registered email id.




Sachin Sharma –
HackLearners you are doing great job nice course
Mahabub jahedi –
Nice 👍
Vishal Bhist –
Best Course